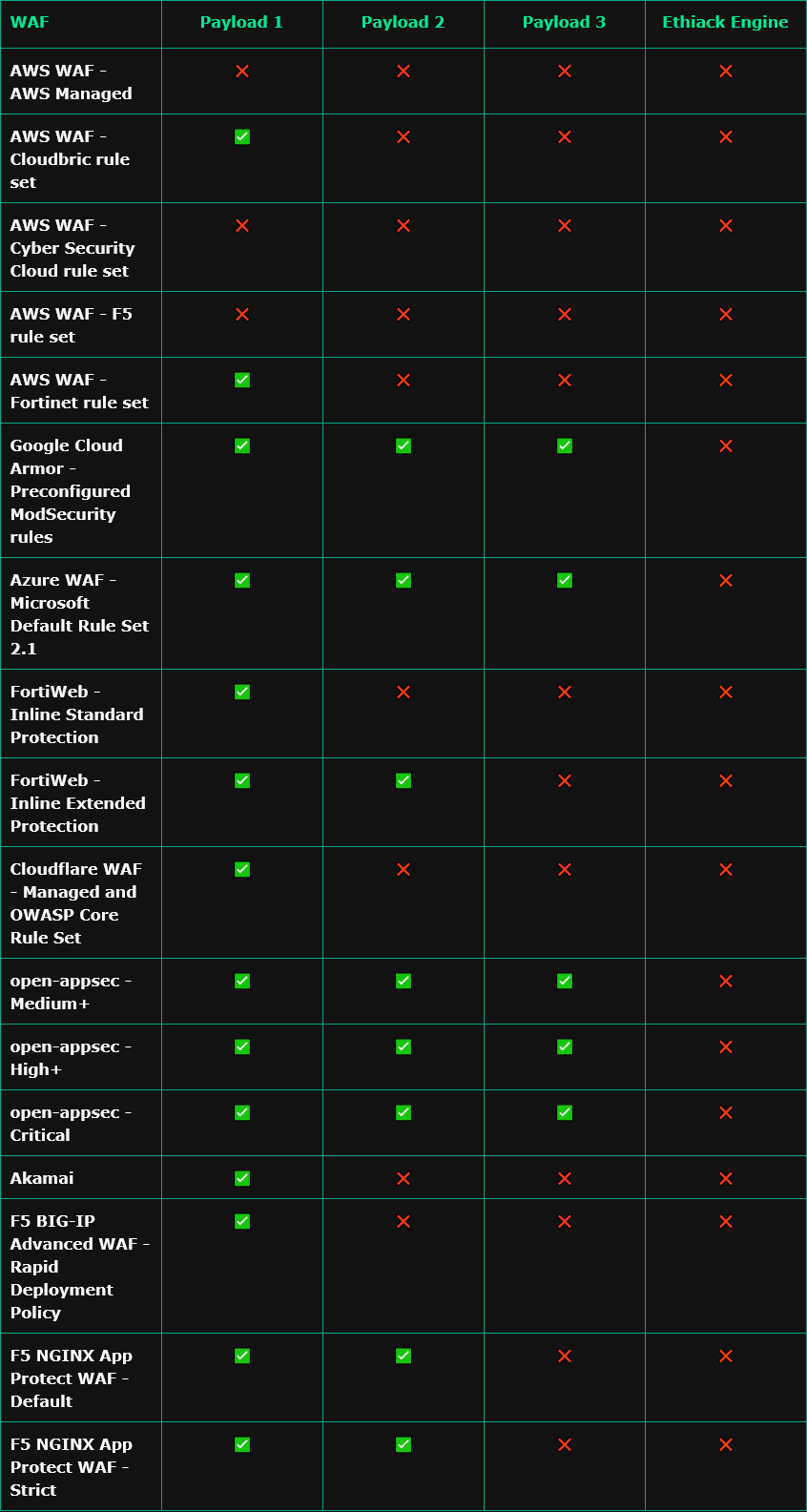
A new exploit allows threat actors to bypass the web application firewalls of nine vendors.
The attack abuses parameter pollution techniques and was found by security firm ETHIACK.
It was tested against 9 WAFs in 17 different configurations.
-1.png)
Bypassing WAFs for Fun and JS Injection with Parameter Pollution
Technical deep dive into bypassing a strict Web Application Firewall using HTTP Parameter Pollution, leveraging multi-parameter payload splitting to achieve JavaScript injection and evade detection.
.png)
(blog.ethiack.com)